Protect from ransomware
We can help build layered defences to protect from ransomware.


How do you protect your business from ransomware infections?
As ransomware can enter your network in multiple ways, there is no ‘silver bullet’ which is guaranteed to prevent ransomware infections. You must have layers of security defences at each potential network entry point.
With Equilibrium’s Ransomware Defence portfolio you can bypass even the most sophisticated ransomware attacks. Our ransomware defence portfolio provides DNS layer, to email, to endpoint protection, to help you remain cyber-resilient and protected from ransomware attacks.
Ransomware is a security roadblock which is here to stay. Though no one ever expects to be hit by such an attack, it is predicted that ransomware hits a new victim every 10 seconds.
Ready to achieve your security goals? We’re at your service.
Whether you are a CISO, an IT Director or a business owner, Equilibrium has the expertise to help you shape and deliver your security strategy.

Defend your business with our Ransomware Defence portfolio
Unfortunately, ransomware is a security roadblock which is here to stay. While new types of attacks like cryptomining have entered the race, ransomware is still a huge obstacle for businesses. To remain protected you must learn how to stay ahead of advanced threats.
Our Ransomware defence portfolio helps to reduce the risk of ransomware infections, and other malware so you can focus on your business’ top priorities. Layers of protection work together to prevent ransomware attacks, detect if they gain access to your systems and contain them to limit damage.
How to prevent ransomware infections
Advanced malware protection can block ransomware from gaining access and encrypting files on endpoint devices. As the ransomware can’t take files hostage, the ransomware attack cannot be conducted.
Our threat-centric approach will give you enhanced security needed in today’s threat landscape. Email is the number one attack vector for ransomware. If you can stop the malicious email from landing in an inbox, you can prevent the attack.
We can help block DNS requests before a user reaches a malicious site hosting ransomware on or off the corporate network. We can also block command and control call-backs which can stop the ransomware in its tracks.
2FA can identify user identity by sending push notifications to mobiles. 2FA stops unauthorised users (hackers) accessing systems and critical applications, meaning Ransomware cannot be distributed onto the network.
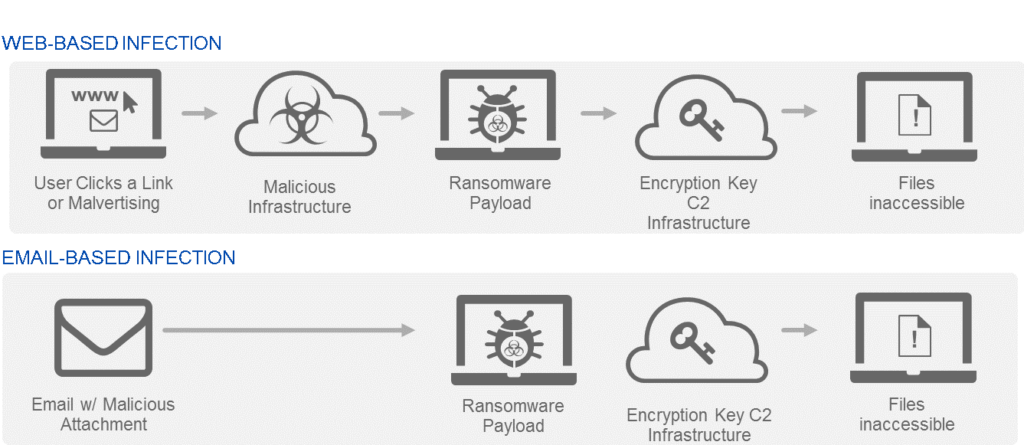
How Ransomware works- Most variants require all 5 steps
Should I pay the ransom?
Do you know what you would do if you saw the dreaded message: ‘your personal files are encrypted, pay the ransom to retrieve your data’? Targeted organisations often believe that paying the ransom is the most cost-effective way to get their data back — and, unfortunately, this may also be the reality. The problem is that every single business that pays to recover their files is directly funding the development of the next generation of ransomware.
As a result, ransomware is evolving at an alarming rate with new and more sophisticated variants. This makes defending your organisation’s data against ransomware more critical than ever. Ransomware attacks have become an extremely lucrative criminal enterprise. While 54% of UK businesses are said to have been hit by a ransomware attack in the past year, over half of these eventually gave in and paid the ransom.
Frequently Asked Questions
We could tell you that we are highly qualified experts, with over 20 years’ experience in the Cyber Security industry. Or that we have a proven track record of implementing effective Cyber Security strategies for NHS trusts, financial organisations, high-street retailers and SME’s.
But we want to show how we stand out from the crowd.
You’re probably more interested in how we can supercharge your security strategy and launch you above and beyond your Cyber Security goals.
Our team are the driving force of your security initiatives. By partnering with us, we don’t just protect your data. We stand with you in the fight against cyber-crime. Our experts are on-hand to help you stay ahead of the curve and build a Cyber Security culture which is part of your company’s fabric.
Should you choose a general IT provider to handle your security, or partner with a dedicated Cyber Security specialist? Whilst a general IT provider may well be the cheaper option, would you trust a dentist to conduct heart surgery, if they were offering the service for half the price?
When it comes to the security of your business, second-rate protection is simply not an option. By partnering with experienced security experts, you can rest assured that your security is in safe, experienced, and dependable hands, and have far less sleepless nights!
We’re not a jack of all trades like a general IT provider. We’re experts in our field and specialise specifically in Cyber Security. The core foundations of Equilibrium were built by technical experts with a background in network security. Which means we don’t simply resell a security product and let the fancy tech do the talking. We know our stuff and have the skillset and experience to prove it.
For us, communication is key to building strong security partnerships. We are told this is a fundamental part of why our customers choose us over our competitors. We pride ourselves on being good listeners, never leaving you in the dark and always taking time to understand the inner workings of your business.
Relax we’ve got this. As an extension of your team, we’re there to offer our extensive industry knowledge, provide innovative solutions and be the driving force of your security strategy.
We’re not a supplier who needs handholding. We’re the helping hand. We understand the importance of having a security partner you can trust to get the job done, on-time and in-budget.
We have an eye for the finer details. For us, it is all about dotting the i’s and crossing the t’s when it comes to the security of your brand.
By combining our technical expertise with our dedication to helping you achieve your Cyber Security goals, we help to leverage your security capability to new heights.
