When you ask a penetration tester what their strategy is for testing, it’s really not an easy question to answer. Testing for vulnerabilities is a bit like navigating a maze for penetration testers. It’s a complex process that involves using all sorts of tactics, techniques, and procedures to make sure everything’s thoroughly checked. It’s all about ensuring that the test is as effective as possible.
A day to day for a pen tester is always different and explaining how they secure such a diverse range of technologies is no small task. It’s like trying to juggle a bunch of different balls at once!
That’s why we’re here to simplify and describe the strategy and thinking behind a penetration test, and to show you how a penetration tester approaches a target application or network, so you can see for yourself how our testers make decisions that allow them to systematically identify vulnerabilities.
First though, a quick explainer is needed…
White, Black, or Grey Penetration Tests:
Penetration tests aren’t black and white, they are also grey (and red, blue and purple, but let’s not confuse things). The context of a test is very important, and each organisation has different needs. According to your strategy and threat model, you might choose either a white, black or grey box penetration test. This is a term that is applied to a test to describe the level of knowledge your tester has about their target:
- Black Box Penetration Testing
In a black box test, our pen tester is operating from a simulated hostile adversaries’ perspective, they are not given any real information about their target other than the minimum amount of information needed to ensure they stay in scope.
This is the most realistic form of penetration testing, as a real adversary would (hopefully) not have any privileged information about their target and would need to figure out as much as they can by interacting with the target before trying to exploit it.
- White Box Penetration Testing
Forming a polar opposite to black box testing, white box penetration testing gives the tester as much information as is available about their testing target, this can include code, documentation and access to internal expert resources provided by the client. They may even be able to create custom builds of applications that allow them to test scenarios that would not be possible were the test to be a black box exercise.
This allows an extremely comprehensive test to be conducted, but is usually higher cost, takes longer and doesn’t give as much of an indication of the vulnerability exposure that can be observed by a less privileged attacker.
- Grey Box Penetration Testing
A grey box aims to be the best of both worlds, it gives our pen tester a reasonable degree of access to information, usually in the form of documentation and the ability to ask questions as needed to your internal resources but doesn’t give complete access to source code.
This allows for a comprehensive test without massive testing budgets and resource commitments. It’s also the most common form of testing that Equilibrium Security conducts.
The Pen Test Strategy Begins:
With an understanding of the different contexts of a test that can be conducted, lets dive into the actual penetration testing strategy that we use in all of our testing skews.
1. Equilibrium’s Penetration Testers begin their walk:
The first step of any penetration testing methodologies is always enumeration, and what I mean by that is exploration of our target.
- When testing a web application, our testers will start by walking the app, meaning they'll go through every single page that they find and click on everything they can find.
- In a network-based test, they'll walk the network instead, which usually means a combination of listening to traffic and scanning machines to see what they are presenting to other computers.
The purpose behind this is to rapidly familiarise oneself with their target, the better one understands something, the easier it is to exploit it, of course.
During this stage our pen testers will also observe things they think warrant investigation. They might see a weird port on a network test, something non-standard. Or on the other side a web app might have a parameter like admin = False, what happens if I change it to true?
The context is also important to consider in this step, on a white box this stage will involve poring over code and documentation for hours but will be naturally shorter on a black box test.
It’s important for our testers to do this stage properly, it’s tempting for them to dash off and test something the second they see it.


2.The Penetration Test methodology needs a plan
If enumeration has been done to a high quality, our testers will now be in a position where they have a solid understanding of the entire system, it’s purpose and where they feel there may be security weaknesses. However, it’s still not time to let loose and start testing.
- Unveiling the Tester's Initial Reconnaissance: Testers at Equilibrium will start to approach their target. It makes no sense to prioritise items that are likely to provide low impact results, we want to find the absolute worst offenders in our target, because that's what the bad guys do!
- Unravelling the Layers, The Multi-Faceted Nature of Impactful Hacks: That said, an impactful hack is rarely just a single issue that is exploited, and what the hack achieves tends to rely on what the application or network is used for. So, our testers at this point may decide that if they can for example, find a way to access another user's information, then they can use a separate exploit to then place some code on an admin user's profile with the goal of stealing their password.
- Emulating Real Threats for Better Results: This mini strategy will just be one of many the tester develops and that informs their testing, this allows them to be more pragmatic and add a degree of realism to a test. We don't want to just find isolated bugs, we want to emulate a real bad actor, and real bad actors are trying to achieve a specific goal, by setting ourselves specific goals we can better demonstrate real risks/impacts and deliver a better test.
3. The Pen Testers begin to hack
At this point, our testers will finally start to explore their test cases, and this is where the pen testing methodology can branch off into the infinite.
Depending on the technology stack, frameworks in use and the specific code written for a web application, there could be many possibilities for types of vulnerabilities that could be present.
In a network test, there is just as much variation as just about any computer system could be a part of the network, including servers hosting web applications that could themselves require a full web application penetration test.
This step is specifically why writing a fully comprehensive explanation of how a test is performed is so difficult, it really does depend on the expertise and experience of the individual testers to be able to adapt to their target and exploit the specific vulnerabilities that are present within it.
There are of course some frameworks and standards that aim to provide a lattice in which testing can remain consistent between testers and ensure a minimum level of coverage, but even within these the actual process of performing the testing is still highly specific to the target.


- The OWASP Top Ten: is a good example of a resource used to help provide consistency between tests, this is a list of the most common vulnerabilities found in web applications, though less understood is that these vulnerabilities are not discrete items that are consistent from one application to another, they are more categories of vulnerability that broadly apply to individual findings from testing.
In this step, the type of test plays a crucial role.
- In a black box test, the exploitation of vulnerabilities relies heavily on inference and assumptions derived from context and experience. Exploitation rarely proceeds smoothly on the first or even the fifteenth attempt. Testers continuously adjust their approach based on feedback from their target, sometimes even deducing the outcome of an attempt from minimal information, such as the response time of a page to a specific input.
- White box testing involves much less guesswork for obvious reasons, while grey box testing falls somewhere in between the two.
4. Do it again, but better!
This is where the real work comes from in the penetration testing methodology.
Each of our pen testers must constantly iterate their testing. Let’s say for example that in the previous step, our tester was exploiting a vulnerability within a network and manages to get access to the account of a HR user.
- The HR user being part of a specific business function has access to resources, systems and applications that they need to do their job.
- Our testers would describe this simply as new attack surface, meaning that all these lovely things the HR user has access to are now available for our testers to find vulnerabilities within. So, they go back to step one again, and walk the new attack surface, then once they think they understand what they’re seeing they make a plan, then once a plan is together it's time to hack.
- Assuming this all goes successfully, lets assume the HR user had access to a system shared with an IT user, our testers will exploit this system and now have an IT user's account and all the associated access, so the process starts over again!


This isn’t just the case within network testing, think about how many web applications you use every day that have multiple user roles. Testers will often iteratively test applications as they move through privilege levels too.
Summarising Penetration Testing Methodologies
The testing methodology is basically a circle, we can sum up the process with a neat little graphic:
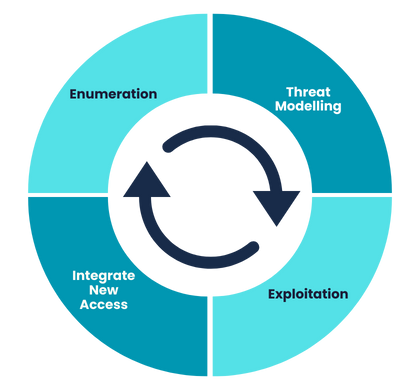
This overview provides a high-level insight into how penetration testers approach various computer systems, illustrating the flexibility required to navigate diverse target sets while adhering to principles that systematically uncover vulnerabilities akin to real threat actors.
For a deeper understanding of the specific steps taken by testers in assessing the security of web applications or networks, materials are being developed to provide a more detailed walkthrough of the process. Given the substantial differences in testing across various target categories, documents will be tailored to outline the process for each major service line.
Want peace of mind knowing your systems are secure?
Contact us to discuss how penetration testing can benefit your organisation today!
We’re here to guide you with your Cyber Security needs. Call us on 0121 663 0055, or email enquiries@equilibrium-security.co.uk.
Don’t leave your Cyber Security to chance. Let’s collaborate to safeguard your digital future.
Ready to achieve your security goals? We’re at your service.
expertise to help you shape and deliver your security strategy.
About the author




